Experts Warn: Three Easy Ways to Infect Your PC With ClickFix
ClickFix malware scam, initially seen in targeted attacks, now widespread. Visitors tricked into downloading password-stealing malware via fake CAPTCHA tests.
“
A sophisticated malware scheme, initially identified in targeted assaults, has now become widespread. This scheme, known as “ClickFix,” tricks visitors to compromised or malicious websites into downloading password-stealing malware by prompting them to press specific keyboard keys that trigger Microsoft Windows actions.
The ClickFix attacks mimic the common “Verify You are a Human” tests used by many websites to differentiate real users from automated bots. This deceptive ploy typically begins with a website popup resembling a CAPTCHA designed to distinguish humans from bots.
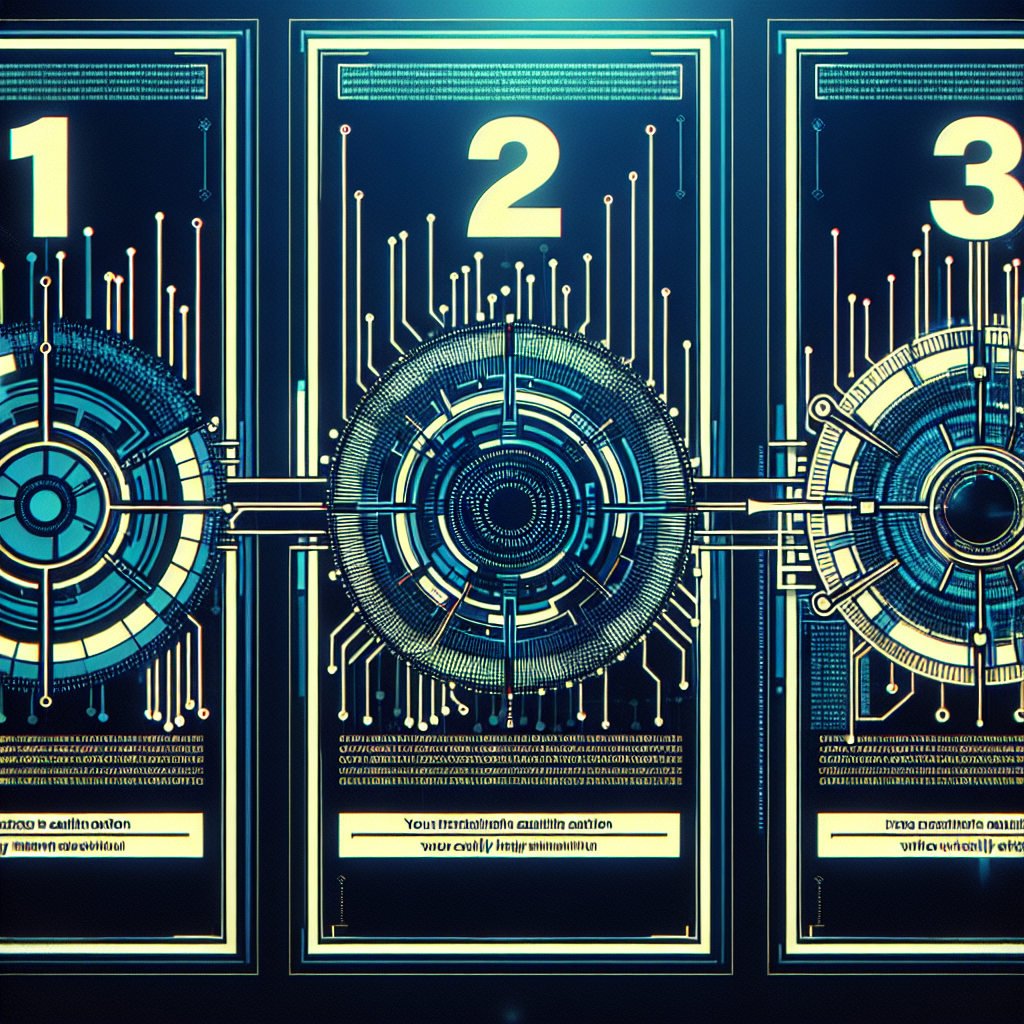
By clicking the “I’m not a robot” button, users are led through three sequential steps to prove their humanity. The first step involves pressing the Windows key and the letter “R” simultaneously, activating a Windows “Run” prompt. The second step requires pressing the “CTRL” key and the letter “V” simultaneously, pasting malicious code from the site’s virtual clipboard. Finally, the third step involves pressing the “Enter” key, triggering the download and execution of malicious code through “mshta.exe,” a Windows program for running Microsoft HTML application files.
This malicious campaign deploys various types of commodity malware, such as XWorm, Lumma stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT, as revealed by Microsoft. The attackers impersonate Booking.com to deceive hospitality industry workers into downloading credential-stealing malware.
Furthermore, ClickFix attacks targeting healthcare workers have been identified using malicious code embedded in the popular physical therapy video site HEP2go. Various forms of ClickFix attacks are reported, including fabricated Google Chrome error pages and fake Facebook prompts.
The ClickFix attack’s reliance on mshta.exe echoes long-standing phishing tactics that embed exploits within Microsoft Office macros. To combat this threat, email security measures have been implemented to deter ClickFix attacks through phishing emails containing HTML attachments masquerading as Microsoft Office files, urging users to click on fake error messages.
Organizations can safeguard against these attacks by implementing Microsoft Group Policy restrictions that prevent the execution of the “run” command when specific keyboard combinations are pressed.
Published on: 2025-03-14 22:15:00 | Author: BrianKrebs